- Home
- Tips & Tricks and news
- Sitecore articles and code samples
- Tip Get the SitecoreAI instance URL from a JWT token
- Using the SitecoreAI Agent API Jobs Feature in Marketplace Apps
- Exploring the SitecoreAI Agent API Jobs Feature
- Hide Wildcard in sitemap.xml with Sitecore MCP Server
- Sitecore Agent API for Sitecore AI
- Wildcards in Sitemap.xml and Sitecore XM Cloud
- From WordPress to Sitecore with SitecoreCommander
- SSO and Sitecore XM Cloud with OpenID Connect
- Content Migration Tip 3 Handling Illegal Characters in Sitecore Serialization
- Content Migration Tip 2 Handling Duplicates in Sitecore Serialization
- Content Migration Tip 1 Handling Clones in Sitecore Serialization
- Tip Unpublish a Language with the Sitecore API
- Sitecore content migration - Part 3 Converting content
- Sitecore content migration - Part 2: Media migration
- Managing Sitecore Item Security Rights with the API
- Find and Optimize Nodes with Over 100 Child Items in Sitecore
- Sitecore System Check PowerShell Report
- Sitecore content migration - Part 1: Media analysis
- Using the Sitecore APIs with Sitecore Commander
- Items as resources part 6 multiple files
- Jan Bluemink Sitecore MVP 2024
- Tip Detecting Sitecore XM Cloud in PowerShell
- Unpublish a language from a Sitecore website
- Media url in the content editor - Edge ready
- Sitecore Content Migrating with GraphQL
- Migrating Your Content
- Create a Package Containing Overridden Items
- Items as resources part 5 Gutter
- Items as resources part 4 compare
- SUGCON Europe 2023 recap
- Item as resources PowerShell warning
- Items as resources part 3 restoring
- Sitecore Webhook Customize JSON
- Jan Bluemink Sitecore MVP 2023
- Sitecore switch Solr indexes strategy on SearchStax
- Sitecore Symposium - laatste ontwikkelingen
- Orphan items and Sitecore Items as resources
- Items as resources part 2 reports
- Tip View html cache content
- Tip Sitecore General link picker 404 error
- Items as resources part 1 warnings
- SUGCON Europe 2022 recap
- From MVC to Sitecore Headless Rendering
- Jan Bluemink Sitecore Most Valuable Professional 2022
- Sitecore Launchpad external link
- The end of Sitecore fast query
- Tip Site specific error and 404 page
- Flush Partial HTML on Dictionary changes
- Sitecore content dependencies options for Partial Html Cache
- Custom Partial Html flush event
- Sitecore Partial HTML Cache
- Flush HTML cache on Sitecore Forms Submit
- Sitecore errors you can encounter
- A poll with Sitecore Forms
- Where is the sitecore_horizon_index
- Sitecore Forms virus upload validation
- Sitecore Forms create a poll
- Sitecore NuGet dependencies in Sitecore 10.1
- Sitecore Forms ML upload validation
- Upgrading to Sitecore 10.1
- Jan Bluemink Sitecore Most Valuable Professional 2021
- Symposium 2020 day 1 Developer recap
- Sitecore CLI login error
- Sitecore Content Editor Warning for large images
- Fix Sitecore 10 Docker installation
- Roles and rights changes in Sitecore 10
- Export and Import Sitecore Roles and Rights
- Advanced Image Field Experience Editor
- Azure DevOps Copy Sitecore Database
- Unable to connect to master or target server
- How many times is each rendering used for a specific website
- A potentially dangerous Request
- CSP headers and Content Hub
- Jan Bluemink Wins Sitecore Most Valuable Professional Award
- Sitecore 9.3 Forms process sensitive files
- Sitecore 9.3 Forms Upload export
- How to add a Sitecore admin programmatically
- DAM connector for Sitecore
- Betty Blocks and Sitecore
- Sitecore Cortex Demo Code in 12 minutes
- Scaling Sitecore JSS images
- Caveats with JSS GraphQL endpoint
- Content tagging JSS GraphQL
- Prevent use of PNG media
- JSS Customizing output
- JSS Integrated GraphQL Queries
- JSS Integrated GraphQL Upgrade
- JSS FormatException: DebugOnly
- New user rights in Sitecore 9.1
- Smartling Translation plugin
- JSS Integrated GraphQL
- Forms Serverless Upload
- Language Warning version 9
- Sitecore Forms Extension Pack
- VSTS and Sitecore
- Roles in Sitecore 9
- Sitecore Azure ARM
- Headless Sitecore
- Sitecore Development 2017
- Azure Cognitive Services
- DocumentDB for sessions
- Databases diskspace tips
- Edit Aliases
- Language Warning
- WFFM and secure Fields
- SUGCON 2016
- Sitecore Tips and Tricks 2016
- SEO Processor
- Custom Cache
- What rights are custom
- Replace Content
- Bulk Create Sitecore Users
- Content editor language
- Roles in Sitecore 8
- Wrong language warning
- Change LinkManager config
- Development and deployment
- Language fallback
- SEO XML Sitemap
- Single line Text with HTML
- Sitecore and the error page
- Sitecore Tips and Tricks
- The Experience Editor
- Upgrade and modules
- User friendly developing
- Dialoge box in een Command
- Editen in de juiste taal
- Sitecore en de error page
- Locked items
- About
- Contact

Created: 20 Jun 2025, last update: 24 Nov 2025
SSO and Sitecore XM Cloud with OpenID Connect, Microsoft Entra ID
Sitecore Cloud Portal now supports both SAML 2.0 and OpenID Connect (OIDC). Because OIDC is JSON based and modern unlike the older, XML/SOAP centric SAML, this post focuses on setting up OpenID Connect with Microsoft Entra ID (formerly Azure Active Directory). The official documentation does a great job covering the basics Configuring OpenID Connect (OIDC). That said, a few practical gotchas only surfaced once I rolled up my sleeves. Below are the lessons I wish I’d had on day one.
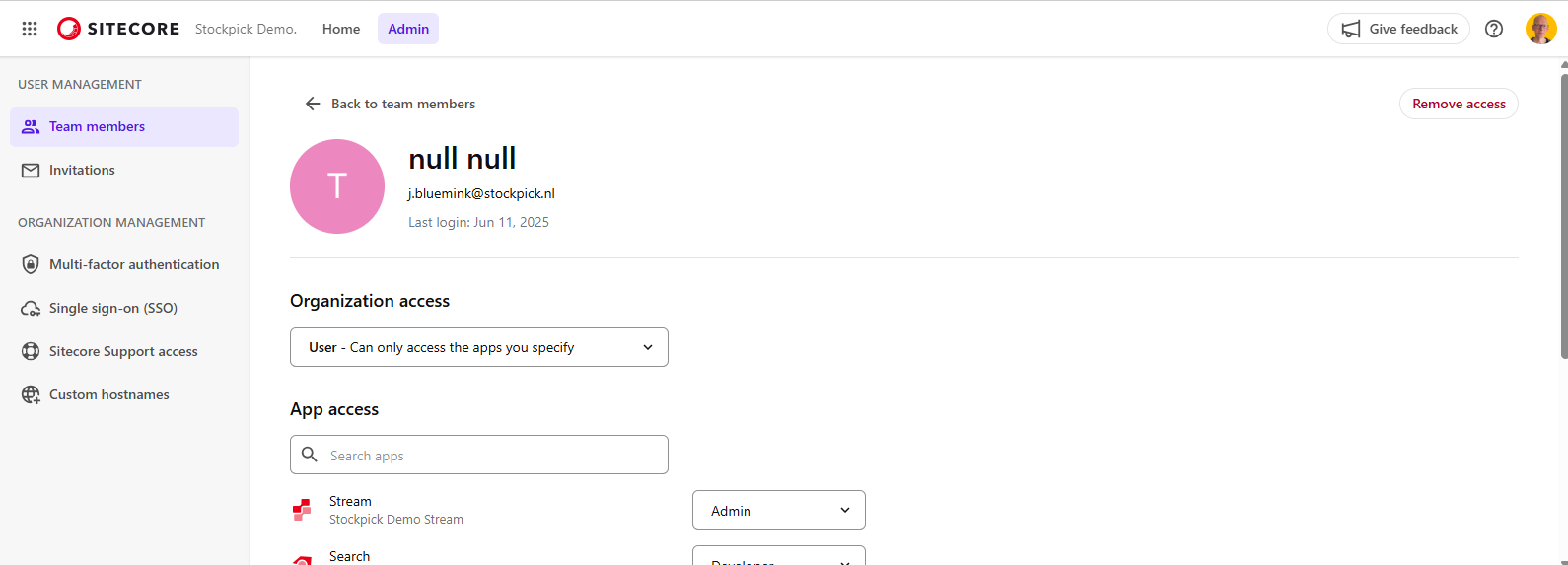
Empty User Name in the Portal
If Given name and Family name show as null, null in the Cloud Portal, features such as Sitecore Stream project can not use fully because they rely on a valid username. The Portal does not allow you to edit those fields directly, they must come from the identity provider.
Fix
1. In the Azure Portal open your Entra ID → App registrations → Your Enterprise App.
2. Go to Token configuration → Add optional claim → ID token → add given_name and family_name.
3. Save and grant admin consent.
Claim mapping is not working
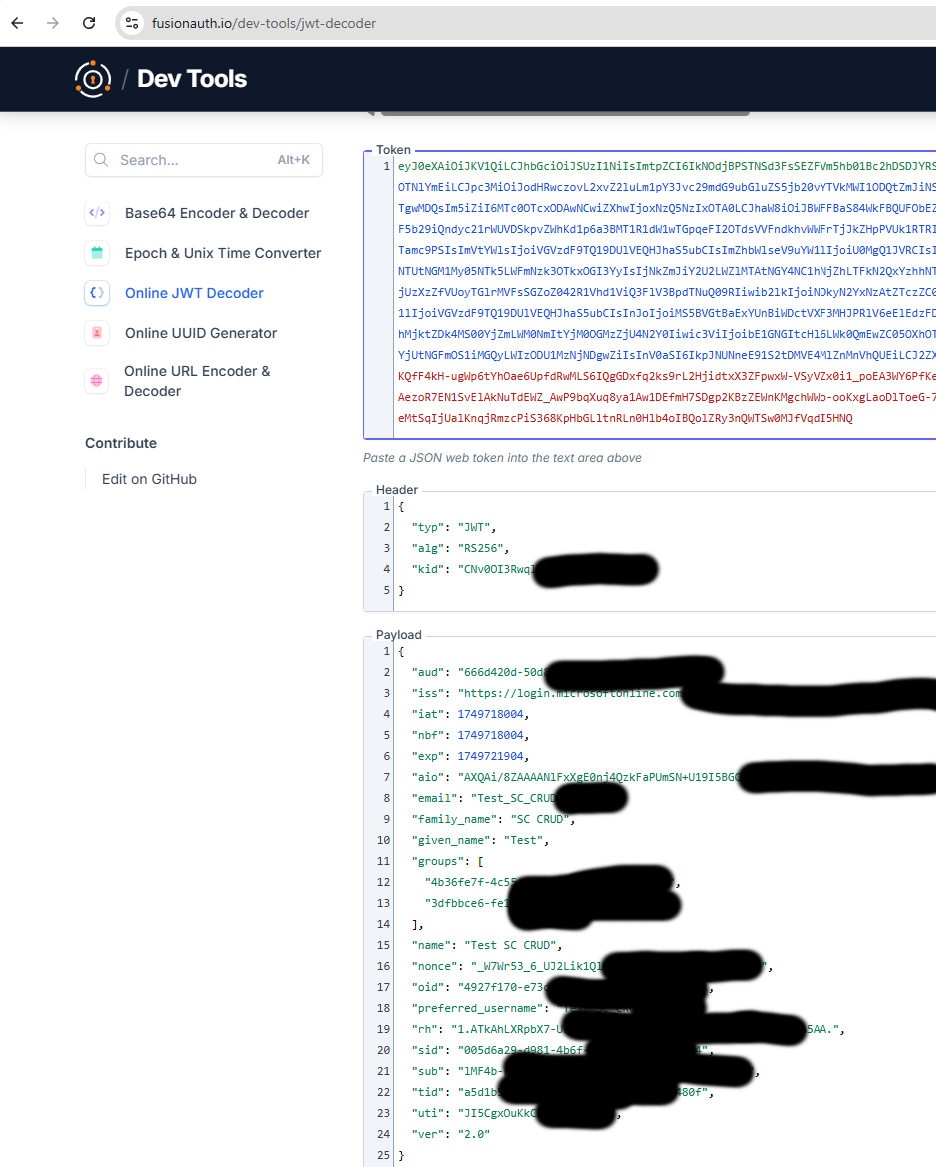
You can confirm which claims you’re getting by decoding the ID token. (In the Portal UI this is Check the mapped claims of your account or simply paste the JWT into jwt.io)
Check which claims you’re getting by decoding the ID token.
You can easily verify which claims are included in your token. Similar to the Sitecore Cloud Portal documentation Check the mapped claims of your account, you can also manually inspect the token returned by Microsoft Entra ID.
To do this, capture the ID token from Entra not Sitecore. (usually found in the payload of the callback request after authentication), and decode it using a tool like jwt.io. This gives you a clear view of all the claims being sent, including optional fields like given_name, family_name, groups, and others that may be essential for your role mapping and login flow.
Claim Mapping Isn’t Working (Groups vs. Group)
When you decode the token you might see a claim called groups that contains GUIDs, e.g.
"groups": [
"4e23c8e1 987b 4a18 b6ed 4b7f1a601234",
"bf2b19ac ..."
]
Sitecore’s documentation example (see Mapping Sitecore ID token claims) uses group (singular) and the display names of the groups. With Entra ID those names are not present unless you add an extra claim.
Fix
Map the claim exactly as it appears: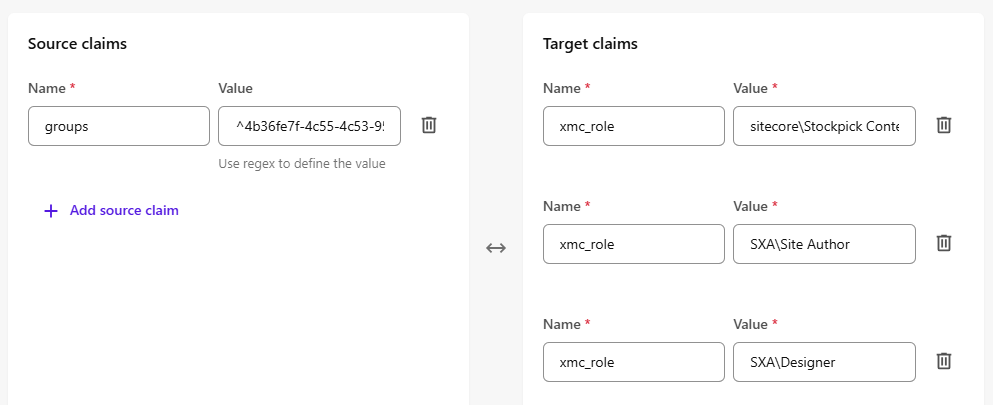
Use groups instead of group and reference the GUIDs in your role mapping file. After that, Sitecore will resolve the roles correctly.
Item Rights Missing in Pages (Bearer Transformation)
Earlier versions of the docs omitted the Bearer identityProvider transformation, which is essential for mapping the virtual roles produced by your claim mapping. Without it, users can log in but won’t see their item level permissions in Pages or other Portal apps.
<identityProvider id="Bearer">
<transformations>
<transformation name="roles" type="Sitecore.Owin.Authentication.Services.DefaultTransformation, Sitecore.Owin.Authentication">
<sources hint="raw:AddSource">
<claim name="con_youridxxx.xmc_role" />
</sources>
<targets hint="raw:AddTarget">
<claim name="http://schemas.microsoft.com/ws/2008/06/identity/claims/role" />
</targets>
<keepSource>true</keepSource>
</transformation>
</transformations>
</identityProvider>
E-mail Address Is Invalid in Sitecore User Manager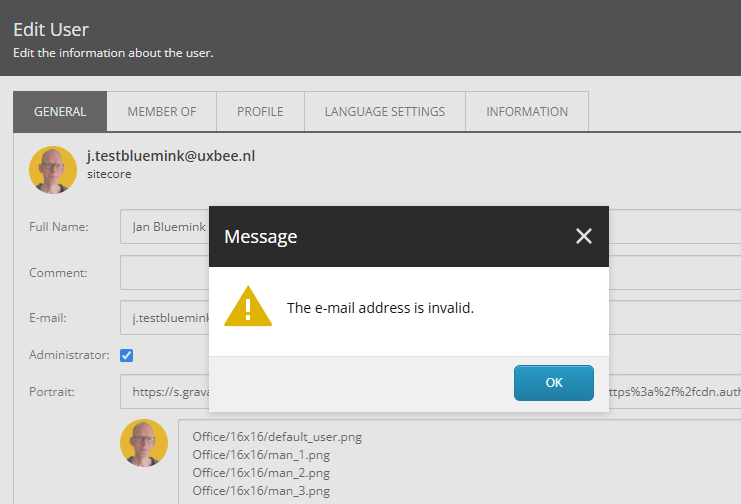
Can not edit user in User Manager in Sitecore. If you need to edit a user inside Sitecore CMS (to set default language, assign custom roles, etc.) you may hit: The e mail address is invalid. Sitecore CMS’s default regex is stricter than the Cloud Portal’s and even stricter than RFC 5322. Addresses like j.bluemink@customer.com fail. Patch it with
<?xml version="1.0" encoding="utf-8"?>
<configuration xmlns:patch="http://www.sitecore.net/xmlconfig/" xmlns:set="http://www.sitecore.net/xmlconfig/set/">
<sitecore>
<settings>
<setting name="EmailValidation">
<patch:attribute name="value">^[a-zA-Z0-9][a-zA-Z0-9._%+\-]*@[a-zA-Z0-9.\-]+\.[a-zA-Z]{2,}$</patch:attribute>
</setting>
</settings>
</sitecore>
</configuration>
Note fixed in:
Base image 1.6.1073 updates
XM Cloud
- Sep 22, 2025
ResolvedImprovement
The latest XM Cloud base image includes the following updates:
-
The User Manager now accepts email addresses with a single character before the dot in the local part (e.g., a.smith@example.com).
Can I disable the SSO after enabling
No only delete.
Can I Enable SSO Only for Test Environment
SSO is enabled at organization level and is tied to one or more e‑mail domains. For testing use the Test button before enabling.



